Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool
Related Articles: Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool
- 2 Introduction
- 3 Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool
- 3.1 Understanding the Mechanics of Nmap
- 3.2 The Power of Nmap in Action: Key Applications
- 3.3 Navigating the Nmap Landscape: Key Features and Commands
- 3.4 Navigating the Nmap Landscape: Key Features and Commands
- 3.5 FAQs about the Nmap Tool
- 3.6 Tips for Using Nmap Effectively
- 3.7 Conclusion: Embracing Nmap as a Powerful Network Security Tool
- 4 Closure
Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool

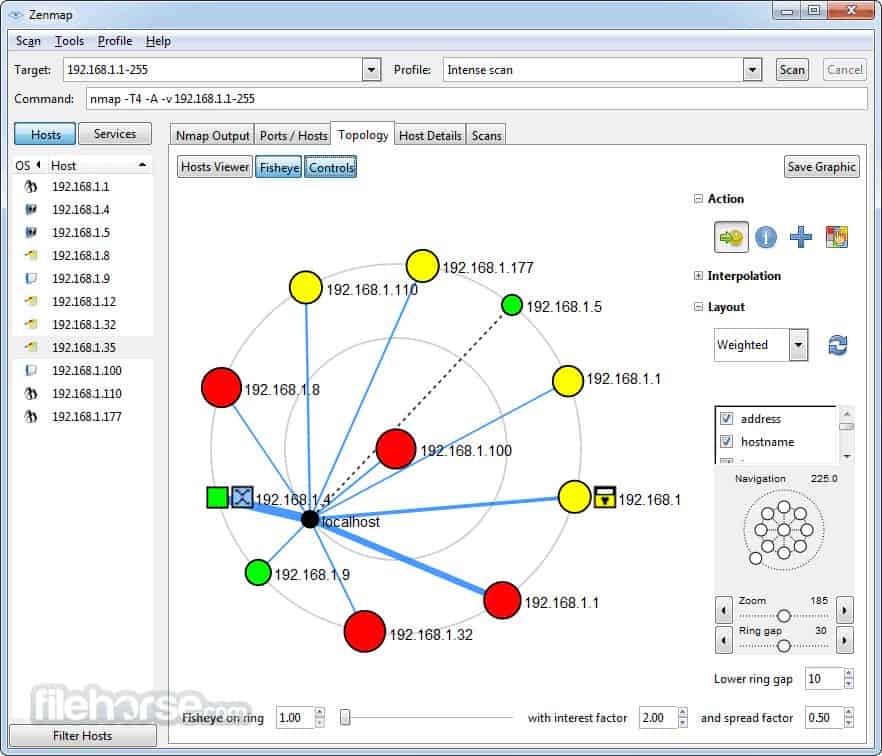
In the intricate world of network security, understanding the landscape of connected devices is paramount. This is where the Nmap tool emerges as a powerful ally, providing comprehensive insights into network topology, service identification, and vulnerability analysis.
Nmap, short for Network Mapper, is a free and open-source utility renowned for its versatility and depth. It acts as a network scanner, enabling users to discover hosts, identify open ports, detect operating systems, and glean crucial information about network services. This information serves as a foundation for various security tasks, from network administration and penetration testing to vulnerability assessment and incident response.
Understanding the Mechanics of Nmap
Nmap operates by sending packets to target hosts and analyzing the responses received. These packets can be crafted to elicit specific responses, allowing Nmap to identify a wide range of network characteristics. The tool utilizes various techniques, including:
- Port Scanning: This involves sending probes to specific ports on a target host to determine which ports are open and listening for connections. Nmap offers a variety of scanning methods, including TCP SYN scan, UDP scan, and stealth scan, each with its own advantages and limitations.
- Operating System Detection: Nmap analyzes the responses from target hosts to identify the operating system running on them. This analysis relies on factors such as TCP/IP stack characteristics, network timing, and specific service responses.
- Service Version Detection: Nmap can identify the version of services running on a target host. This information is crucial for understanding potential vulnerabilities and identifying outdated software.
- Network Mapping: Nmap can be used to map the entire network topology, identifying all connected hosts and their relationships. This information is valuable for network administration and security audits.
The Power of Nmap in Action: Key Applications
The applications of Nmap extend far beyond basic network discovery. Here are some of the key areas where this tool shines:
1. Network Security Auditing: Nmap plays a crucial role in identifying potential security vulnerabilities within a network. By scanning for open ports, detecting outdated services, and identifying vulnerable operating systems, security professionals can pinpoint weaknesses that could be exploited by attackers.
2. Vulnerability Assessment: Nmap can be used to identify known vulnerabilities in network devices and applications. This information can be used to prioritize patching efforts and mitigate risks.
3. Penetration Testing: Nmap is a valuable tool for penetration testing, enabling ethical hackers to simulate real-world attacks and identify security flaws.
4. Network Administration: Nmap is a powerful tool for network administrators, enabling them to gain a comprehensive understanding of their network infrastructure, identify misconfigured devices, and troubleshoot connectivity issues.
5. Incident Response: In the event of a security breach, Nmap can be used to identify the source of the attack, track the attacker’s movements, and gather evidence for incident response.
6. Research and Development: Nmap is widely used by security researchers and developers to study network protocols, analyze security vulnerabilities, and develop new security tools.
Navigating the Nmap Landscape: Key Features and Commands
Nmap’s power lies in its versatility and the vast array of features and commands it offers. Here are some of the key features and commands that empower users to conduct sophisticated network scans:
1. Scan Types: Nmap offers a wide range of scan types, each designed for specific purposes. Some of the most common scan types include:
- TCP SYN Scan: A stealthy scan that sends a SYN packet to each port and waits for a SYN-ACK response. This scan does not establish a full connection, making it less likely to be detected by intrusion detection systems.
- UDP Scan: This scan sends UDP packets to target ports and analyzes the responses. UDP scans are typically slower than TCP scans due to the lack of a handshake mechanism.
- Stealth Scan: This scan utilizes the TCP connect() function to establish a connection to the target port. It is similar to a TCP connect scan but avoids sending a SYN packet, making it more stealthy.
- FIN Scan: This scan sends a FIN packet to each port and analyzes the response. A FIN packet should be rejected by a closed port, but a different response might indicate an open port.
- Xmas Scan: This scan sends a packet with the FIN, PSH, and URG flags set. It is similar to a FIN scan but provides additional information about the target port.
2. Scripting Engine: Nmap’s scripting engine enables users to automate complex network scans and analyze the results. These scripts can perform various tasks, such as identifying vulnerabilities, performing specific service checks, and extracting information from network devices.
3. Output Formats: Nmap offers a variety of output formats, allowing users to tailor the results to their specific needs. These formats include:
- Normal Output: This is the default output format, providing a summary of the scan results.
- XML Output: This format provides a structured representation of the scan results, making it suitable for automated analysis and reporting.
- Grepable Output: This format provides a text-based output that is easily parsed by other tools.
4. Nmap Command-Line Syntax: Nmap’s command-line syntax is powerful and flexible, allowing users to customize their scans with a wide range of options. Some of the common command-line options include:
- -sT: Perform a TCP SYN scan.
- -sU: Perform a UDP scan.
- -sS: Perform a stealth scan.
- -p: Specify the port range to scan.
- -O: Perform operating system detection.
- -v: Increase verbosity level.
- -oX: Save the output in XML format.
- -oG: Save the output in grepable format.
Navigating the Nmap Landscape: Key Features and Commands
Nmap’s power lies in its versatility and the vast array of features and commands it offers. Here are some of the key features and commands that empower users to conduct sophisticated network scans:
1. Scan Types: Nmap offers a wide range of scan types, each designed for specific purposes. Some of the most common scan types include:
- TCP SYN Scan: A stealthy scan that sends a SYN packet to each port and waits for a SYN-ACK response. This scan does not establish a full connection, making it less likely to be detected by intrusion detection systems.
- UDP Scan: This scan sends UDP packets to target ports and analyzes the responses. UDP scans are typically slower than TCP scans due to the lack of a handshake mechanism.
- Stealth Scan: This scan utilizes the TCP connect() function to establish a connection to the target port. It is similar to a TCP connect scan but avoids sending a SYN packet, making it more stealthy.
- FIN Scan: This scan sends a FIN packet to each port and analyzes the response. A FIN packet should be rejected by a closed port, but a different response might indicate an open port.
- Xmas Scan: This scan sends a packet with the FIN, PSH, and URG flags set. It is similar to a FIN scan but provides additional information about the target port.
2. Scripting Engine: Nmap’s scripting engine enables users to automate complex network scans and analyze the results. These scripts can perform various tasks, such as identifying vulnerabilities, performing specific service checks, and extracting information from network devices.
3. Output Formats: Nmap offers a variety of output formats, allowing users to tailor the results to their specific needs. These formats include:
- Normal Output: This is the default output format, providing a summary of the scan results.
- XML Output: This format provides a structured representation of the scan results, making it suitable for automated analysis and reporting.
- Grepable Output: This format provides a text-based output that is easily parsed by other tools.
4. Nmap Command-Line Syntax: Nmap’s command-line syntax is powerful and flexible, allowing users to customize their scans with a wide range of options. Some of the common command-line options include:
- -sT: Perform a TCP SYN scan.
- -sU: Perform a UDP scan.
- -sS: Perform a stealth scan.
- -p: Specify the port range to scan.
- -O: Perform operating system detection.
- -v: Increase verbosity level.
- -oX: Save the output in XML format.
- -oG: Save the output in grepable format.
FAQs about the Nmap Tool
1. What are the prerequisites for using Nmap?
Nmap is a command-line tool, requiring familiarity with basic command-line operations. It can be run on various operating systems, including Windows, macOS, Linux, and Unix.
2. Is Nmap legal to use?
Nmap itself is a legitimate tool used for network security assessments and troubleshooting. However, its misuse for unauthorized scanning or attacks can be illegal. It’s crucial to respect network security policies and obtain necessary permissions before scanning any network.
3. What are the limitations of Nmap?
While powerful, Nmap has limitations:
- Firewall and IDS Evasion: Nmap can be detected by firewalls and intrusion detection systems, which can hinder its effectiveness.
- Scanning Large Networks: Scanning large networks can be time-consuming, and Nmap might not be the most efficient tool for such tasks.
- Limited Visibility: Nmap might not be able to detect all devices on a network, especially those behind firewalls or using complex network configurations.
4. How can I learn more about Nmap?
Nmap has extensive documentation available on its official website: https://nmap.org/. Additionally, numerous online resources, tutorials, and communities dedicated to Nmap can provide valuable insights and guidance.
Tips for Using Nmap Effectively
1. Start with Simple Scans: Begin with basic scans to gain a general understanding of the network before delving into more complex scans.
2. Utilize Scripting Capabilities: Leverage Nmap’s scripting engine to automate repetitive tasks and enhance the efficiency of your scans.
3. Choose Appropriate Scan Types: Select the scan type that best suits your needs, considering factors such as stealthiness, speed, and accuracy.
4. Analyze Output Carefully: Pay attention to the output generated by Nmap, looking for anomalies, vulnerabilities, and potential security risks.
5. Stay Informed: Regularly update Nmap to benefit from new features, bug fixes, and security enhancements.
Conclusion: Embracing Nmap as a Powerful Network Security Tool
Nmap stands as a cornerstone in the world of network security, empowering individuals and organizations to gain valuable insights into their network infrastructure. Its versatility, depth, and open-source nature make it a valuable tool for security professionals, network administrators, and researchers alike. Whether you’re performing security audits, conducting penetration tests, or simply gaining a better understanding of your network, Nmap provides the tools and information necessary to make informed decisions and enhance network security. By mastering its features and leveraging its capabilities, you can unlock the power of network discovery and navigate the complexities of the digital landscape with greater confidence and security.




Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Network Discovery: A Comprehensive Guide to the Nmap Tool. We hope you find this article informative and beneficial. See you in our next article!
