Unveiling Network Secrets: A Comprehensive Guide to Nmap
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap
Introduction
With great pleasure, we will explore the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap
- 2 Introduction
- 3 Unveiling Network Secrets: A Comprehensive Guide to Nmap
- 3.1 Understanding Nmap’s Core Functionality
- 3.2 Nmap in Action: A Practical Demonstration
- 3.3 Diving Deeper: Advanced Nmap Techniques
- 3.4 Nmap’s Role in Security Assessments
- 3.5 Nmap: A Tool for Ethical Hackers
- 3.6 Nmap: Beyond Security
- 3.7 FAQs about Nmap
- 3.8 Tips for Effective Nmap Usage
- 3.9 Conclusion
- 4 Closure
Unveiling Network Secrets: A Comprehensive Guide to Nmap
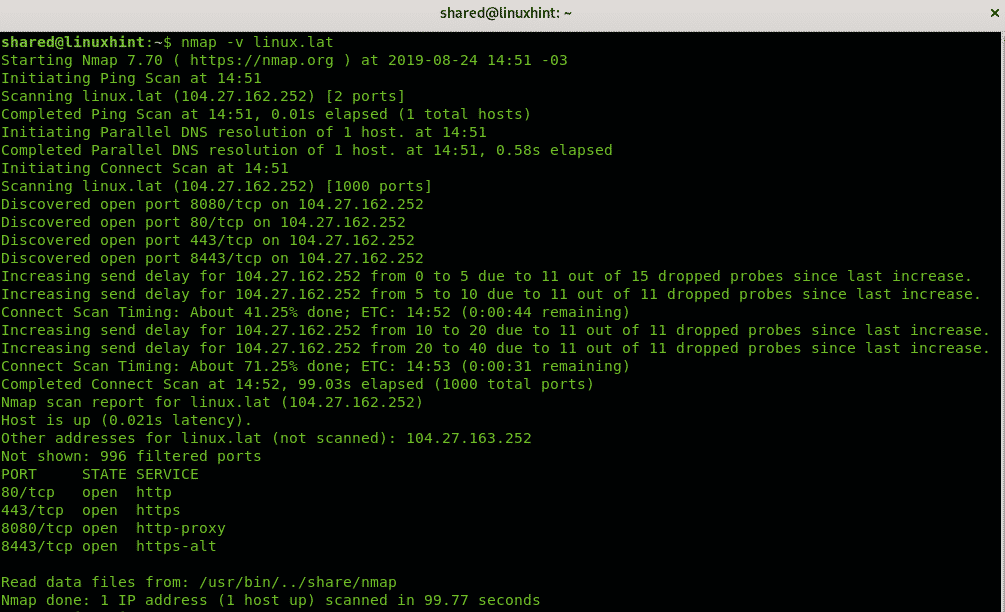
Nmap, short for Network Mapper, is a powerful open-source tool that has become indispensable for network administrators, security professionals, and penetration testers alike. Its versatility lies in its ability to scan networks, identify active hosts, map network services, and gather crucial information about network infrastructure. This comprehensive guide aims to demystify Nmap, providing a practical understanding of its capabilities and demonstrating its application through real-world scenarios.
Understanding Nmap’s Core Functionality
Nmap operates by sending specially crafted packets to target hosts and analyzing the responses. These responses reveal valuable insights about the network, including:
- Host Discovery: Nmap can identify active hosts on a network, even if they are not actively responding to standard ping requests. This is achieved through various techniques like port scanning, SYN scanning, and ICMP ping sweeps.
- Service Detection: Nmap can pinpoint the services running on identified hosts, along with their versions, operating systems, and other relevant details. This information is crucial for understanding the network’s security posture and potential vulnerabilities.
- Operating System Fingerprinting: Nmap can often accurately determine the operating system running on a host based on its responses to specific network probes. This information is invaluable for tailoring security assessments and exploitation attempts.
- Network Mapping: Nmap can visualize the network topology by identifying connections between hosts, revealing the network’s structure and identifying potential bottlenecks or points of vulnerability.
Nmap in Action: A Practical Demonstration
To illustrate Nmap’s capabilities, let’s consider a simple example. Imagine you are a network administrator tasked with identifying all active hosts on your company’s network and determining the services they offer.
1. Host Discovery:
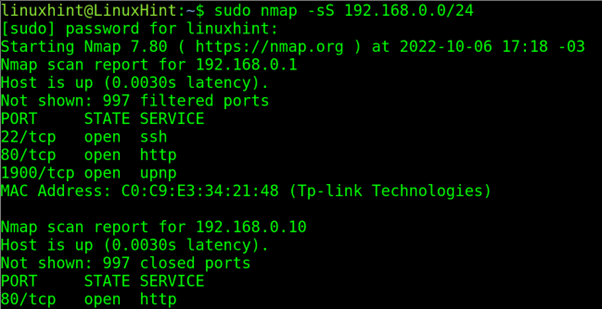
The most basic Nmap command for host discovery is nmap -T4 192.168.1.0/24. This command instructs Nmap to scan the entire 192.168.1.0/24 subnet using a speed setting of 4 (medium speed). The output will display a list of active hosts within the subnet, along with their IP addresses and MAC addresses.
2. Service Detection:
To identify the services running on a specific host, you can use the -sV flag. For example, nmap -sV 192.168.1.10 will scan the host at 192.168.1.10 and attempt to identify the services running on its open ports. The output will include details like the service name, version, and banner information.
3. Operating System Fingerprinting:
Nmap’s -O flag enables operating system fingerprinting. Running nmap -O 192.168.1.10 will probe the host with specific packets designed to identify the operating system based on its responses. The output will provide a list of potential operating systems, ranked by their likelihood.
4. Network Mapping:
Nmap’s -T flag allows you to visualize the network topology. Running nmap -T4 192.168.1.0/24 will produce a map of the network, showing the connections between hosts and the services they offer.
Diving Deeper: Advanced Nmap Techniques
Nmap offers a wide range of advanced techniques that cater to specific use cases. Some notable features include:
- Script Scanning: Nmap’s scripting engine allows users to run scripts that perform specific tasks, such as vulnerability checks, service enumeration, or custom probes. This provides immense flexibility and allows users to tailor Nmap to their specific needs.
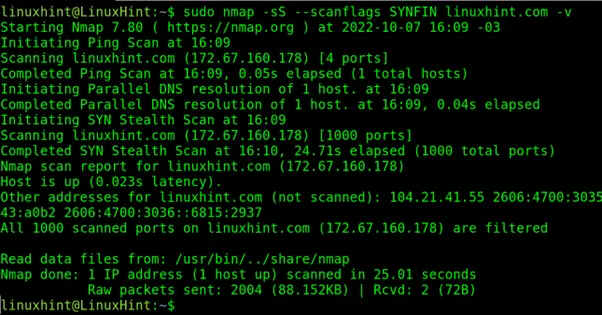
- Stealth Scanning: Nmap offers stealth scanning options that minimize the chances of detection by firewalls or intrusion detection systems. This is achieved by using techniques like SYN scanning, which avoids sending full TCP packets.
- Time-Based Scanning: Nmap allows for time-based scanning, which can be useful for identifying hosts that are only active during specific timeframes. This technique is particularly relevant for detecting hosts that are only online during specific hours or days.
- Custom Port Scanning: Nmap allows users to specify the ports they want to scan, instead of relying on default port ranges. This is useful for focusing on specific services or ports that are relevant to the current investigation.
- Output Formatting: Nmap offers various output formats, including plain text, XML, and greppable output, allowing users to tailor the output to their specific needs and integrate it with other tools.
Nmap’s Role in Security Assessments
Nmap plays a crucial role in security assessments by providing valuable information about a target network’s vulnerabilities. This information can be used to:
- Identify Open Ports and Services: Nmap helps pinpoint open ports and services that might be vulnerable to attacks. This allows security professionals to prioritize remediation efforts and focus on the most critical vulnerabilities.
- Discover Hidden Hosts: Nmap’s ability to detect hidden hosts can reveal previously unknown assets within a network, providing crucial insights into the network’s security posture and potential attack vectors.
- Analyze Network Topology: Nmap’s network mapping capabilities help visualize the network’s structure and identify potential points of weakness, such as poorly configured firewalls or vulnerable network devices.
- Perform Vulnerability Scans: Nmap’s scripting engine allows users to run scripts that perform vulnerability checks, identifying potential exploits and weaknesses in the target network.
Nmap: A Tool for Ethical Hackers
Nmap is a powerful tool for ethical hackers who conduct penetration testing. It allows them to:
- Identify Potential Attack Vectors: Nmap helps ethical hackers identify potential attack vectors by scanning for open ports, services, and vulnerable systems.
- Simulate Real-World Attacks: Nmap’s scripting engine allows ethical hackers to simulate real-world attacks, testing the target’s security posture and identifying potential weaknesses.
- Gather Information for Exploit Development: Nmap provides valuable information about the target network’s infrastructure, operating systems, and services, which can be used to develop and test exploits.
Nmap: Beyond Security
While Nmap is primarily known for its security applications, it also proves valuable in other domains, including:
- Network Management: Nmap helps network administrators identify active hosts, map network topology, and gather information about network devices, facilitating efficient network management and troubleshooting.
- Troubleshooting: Nmap can be used to identify network issues by detecting connectivity problems, identifying overloaded devices, or pinpointing the source of network traffic.
- Research: Researchers use Nmap to gather data about network infrastructure, analyze network traffic patterns, and study network security trends.
FAQs about Nmap
1. Is Nmap legal to use?
Yes, Nmap is a legitimate tool used for ethical purposes, such as network administration, security assessments, and research. However, using Nmap for malicious purposes, such as unauthorized scanning or denial-of-service attacks, is illegal.
2. How can I learn more about Nmap?
Nmap’s official website (https://nmap.org/) offers extensive documentation, tutorials, and resources for learning about its capabilities and usage. Additionally, numerous online forums and communities dedicated to Nmap provide valuable insights and support.
3. Can Nmap be used for automated scanning?
Yes, Nmap can be used for automated scanning through scripting and integration with other tools. This enables users to perform repetitive scans, analyze large networks, and automate specific tasks.
4. What are some common Nmap commands?
-
nmap -T4 192.168.1.0/24: Scans the entire 192.168.1.0/24 subnet for active hosts. -
nmap -sV 192.168.1.10: Identifies the services running on the host at 192.168.1.10. -
nmap -O 192.168.1.10: Attempts to fingerprint the operating system running on the host at 192.168.1.10. -
nmap -T4 192.168.1.0/24 -oA output.txt: Scans the subnet and saves the output to a file named output.txt in various formats.
5. How can I protect my network from Nmap scans?
- Firewall Configuration: Configure firewalls to block incoming traffic from unauthorized sources.
- Intrusion Detection Systems (IDS): Implement IDS to monitor network traffic and detect suspicious activities, including Nmap scans.
- Port Hardening: Close unnecessary ports to minimize the attack surface.
- Operating System Updates: Keep operating systems and applications up-to-date to patch known vulnerabilities.
Tips for Effective Nmap Usage
- Start with basic commands: Begin with simple commands to understand Nmap’s functionality before venturing into advanced techniques.
- Experiment with different scan types: Explore various scan types, such as SYN scanning, stealth scanning, and time-based scanning, to tailor your scans to specific scenarios.
- Utilize scripting: Leverage Nmap’s scripting engine to automate tasks, perform custom checks, and extend Nmap’s capabilities.
- Review and analyze output: Carefully review the output of Nmap scans to identify key information, potential vulnerabilities, and actionable insights.
- Stay informed about updates: Regularly check for updates and new features to ensure you are utilizing the latest capabilities of Nmap.
Conclusion
Nmap is a powerful and versatile tool that empowers individuals and organizations to gain comprehensive insights into their networks. Its ability to discover hosts, identify services, fingerprint operating systems, and map network topology makes it an indispensable tool for network administrators, security professionals, and penetration testers alike. By understanding Nmap’s core functionality, exploring advanced techniques, and utilizing its scripting capabilities, users can unlock its full potential and leverage it for a wide range of network-related tasks.



Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap. We thank you for taking the time to read this article. See you in our next article!
