Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts
Related Articles: Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts
- 2 Introduction
- 3 Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts
- 3.1 Understanding Nmap Scripts: A Deeper Dive
- 3.2 The Benefits of Utilizing Nmap Scripts
- 3.3 Exploring the World of Nmap Scripts: Categories and Applications
- 3.4 Getting Started with Nmap Scripts: A Beginner’s Guide
- 3.5 Frequently Asked Questions (FAQs) about Nmap Scripts
- 3.6 Tips for Effective Nmap Scripting
- 3.7 Conclusion: The Power of Nmap Scripts in Network Security
- 4 Closure
Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts

Nmap, the Network Mapper, stands as a cornerstone of network security auditing and reconnaissance. While Nmap’s core functionality allows for robust port scanning and host discovery, its true potential lies in its scripting engine. Nmap scripts offer a powerful and flexible mechanism to extend Nmap’s capabilities beyond basic scanning, enabling users to perform specialized tasks, automate complex workflows, and gain deeper insights into network vulnerabilities.
Understanding Nmap Scripts: A Deeper Dive
Nmap scripts are essentially small programs written in the Lua scripting language. They leverage Nmap’s powerful API, allowing them to interact with the scanning process, analyze data gathered during scans, and even modify Nmap’s behavior. This flexibility makes them invaluable tools for network security professionals, penetration testers, and anyone seeking to gain a comprehensive understanding of their network environment.
The Benefits of Utilizing Nmap Scripts
-
Automation: Nmap scripts streamline repetitive tasks, automating complex scans and reducing the time and effort required for network analysis. This efficiency allows security professionals to focus on more strategic activities.
-
Enhanced Scanning Capabilities: Scripts extend Nmap’s capabilities beyond basic port scanning. They enable users to perform specialized scans, such as detecting specific services, identifying vulnerabilities, and even launching automated attacks (with ethical considerations in mind).
-
Customizability: Nmap’s scripting engine provides unparalleled flexibility. Users can write their own scripts tailored to their specific needs, allowing for highly customized network analysis and security assessments.
-
Increased Efficiency: Scripts can significantly reduce the time and effort required for network analysis. They can automate repetitive tasks, collect specific data, and even generate reports, freeing up valuable time for security professionals.
-
Improved Accuracy: Scripts help to ensure the accuracy and reliability of network analysis by automating tasks and providing standardized outputs. This consistency is crucial for making informed security decisions.
Exploring the World of Nmap Scripts: Categories and Applications
Nmap scripts are categorized into various groups, each tailored to specific purposes:
1. Vulnerability Detection: These scripts focus on identifying known vulnerabilities in services and applications running on target hosts. They leverage databases of common vulnerabilities and exploit attempts to assess the security posture of a network.
2. Service Detection: This category includes scripts designed to identify and classify specific services running on target hosts. They can provide detailed information about service versions, configurations, and even potential security risks associated with those services.
- Operating System Detection: These scripts leverage fingerprint analysis to identify the operating system running on target hosts. They can detect the specific version of the operating system, potentially revealing vulnerabilities specific to that version.
4. Network Mapping: Scripts in this category focus on mapping out the network topology. They can identify network devices, discover relationships between them, and even create visual representations of the network structure.
5. Enumeration: These scripts are designed to gather detailed information about target hosts, including user accounts, shared resources, and network configurations. They can be used to identify potential security risks and vulnerabilities associated with these assets.
6. Exploitation: While Nmap scripts can be used for ethical hacking and penetration testing, it’s crucial to use them responsibly and only with proper authorization. These scripts can be used to test vulnerabilities and assess the effectiveness of security measures.
Getting Started with Nmap Scripts: A Beginner’s Guide
-
Understanding the Basics: Familiarize yourself with the Lua scripting language, Nmap’s scripting API, and the structure of Nmap scripts.
-
Exploring the Nmap Script Library: Nmap comes with a comprehensive library of scripts covering a wide range of functionalities. Explore the library to understand the available options and identify scripts relevant to your needs.
-
Writing Custom Scripts: Once you’ve gained a basic understanding of Nmap scripting, you can start writing your own scripts tailored to your specific requirements.
-
Leveraging Nmap’s Documentation: Nmap provides extensive documentation on its scripting engine, including examples, tutorials, and API references.
-
Joining the Community: Engage with the Nmap community through forums and mailing lists to seek guidance, share knowledge, and learn from experienced users.
Frequently Asked Questions (FAQs) about Nmap Scripts
1. How do I use Nmap scripts?
To use Nmap scripts, simply include them in your Nmap scan command using the --script option. For example, to run the http-title script, you would use the following command:
nmap -sV --script http-title <target>2. Where can I find Nmap scripts?
Nmap comes with a comprehensive library of scripts, which can be accessed by running nmap --script=help. You can also find additional scripts in the Nmap repository on GitHub.
3. How do I write my own Nmap scripts?
Writing Nmap scripts requires familiarity with the Lua scripting language and Nmap’s scripting API. Nmap provides extensive documentation on its scripting engine, including examples and tutorials.
4. Are Nmap scripts safe to use?
Nmap scripts can be used for both ethical and unethical purposes. It’s crucial to use them responsibly and only with proper authorization. Be aware of the potential risks associated with using scripts for malicious activities.
5. How can I learn more about Nmap scripting?
Nmap’s official documentation is an excellent resource for learning about its scripting engine. You can also find numerous tutorials and resources online, including those on the Nmap community forums and GitHub repositories.
Tips for Effective Nmap Scripting
-
Understand the Purpose: Before using a script, clearly define its purpose and ensure it aligns with your security goals.
-
Choose the Right Scripts: Select scripts that are relevant to your needs and avoid using scripts that may compromise the security of your network.
-
Test Thoroughly: Before using scripts on production networks, thoroughly test them in a controlled environment to ensure they function as expected and do not cause unintended consequences.
-
Document Your Findings: Carefully document the results of your scans, including the scripts used, the findings, and any actions taken based on those findings.
-
Stay Updated: Nmap is constantly being updated with new features and scripts. Stay informed about the latest developments to leverage the most effective tools for your security assessments.
Conclusion: The Power of Nmap Scripts in Network Security
Nmap scripts represent a powerful extension of Nmap’s capabilities, empowering users to perform specialized scans, automate complex workflows, and gain deeper insights into network vulnerabilities. By leveraging the flexibility and versatility of Nmap’s scripting engine, security professionals can enhance their network security assessments, streamline their workflows, and ultimately strengthen the security posture of their networks. As the landscape of network security continues to evolve, Nmap scripts remain an indispensable tool for anyone seeking to understand, analyze, and protect their network environments.


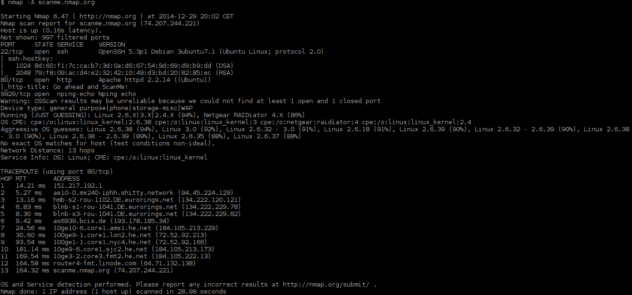


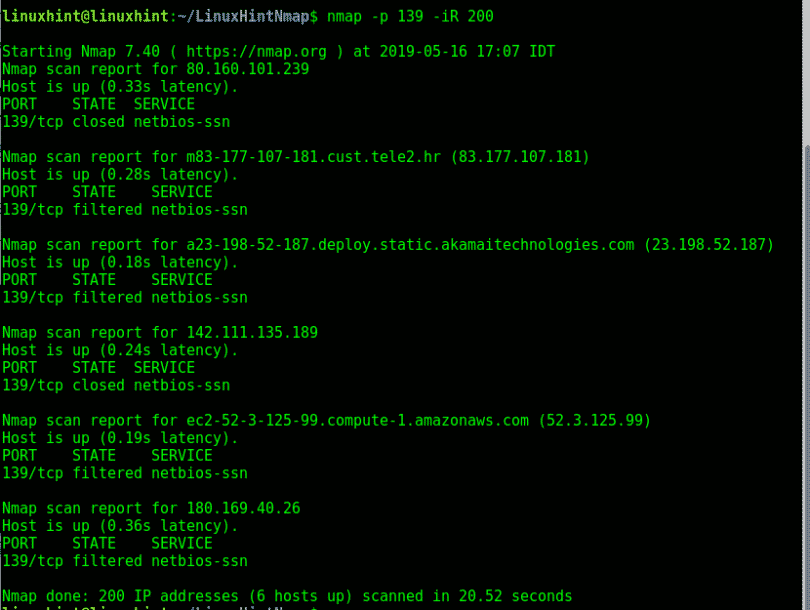

Closure
Thus, we hope this article has provided valuable insights into Unlocking the Power of Nmap: A Comprehensive Guide to Nmap Scripts. We thank you for taking the time to read this article. See you in our next article!
