Nmap: A Powerful Tool for Network Exploration and Security Auditing on Windows
Related Articles: Nmap: A Powerful Tool for Network Exploration and Security Auditing on Windows
Introduction
With great pleasure, we will explore the intriguing topic related to Nmap: A Powerful Tool for Network Exploration and Security Auditing on Windows. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: A Powerful Tool for Network Exploration and Security Auditing on Windows
Nmap, short for Network Mapper, is a versatile and indispensable tool for network administrators, security professionals, and anyone seeking to gain a comprehensive understanding of their network environment. It is a free and open-source utility that empowers users to scan networks, identify active hosts, discover open ports, and gather valuable information about the services running on those ports.
While Nmap is commonly associated with Linux environments, it is also readily available for Windows users. This article delves into the capabilities of Nmap on Windows, exploring its functionalities, benefits, and practical applications.
Understanding Nmap’s Capabilities
Nmap’s core functionality revolves around network scanning. It utilizes various techniques to probe networks and gather information about the devices connected to them. This information can include:
- Host Discovery: Identifying active hosts on a network, even if they are not actively responding to standard requests.
- Port Scanning: Determining which ports on a host are open and listening for connections.
- Service Detection: Identifying the specific services running on open ports, such as web servers, databases, or email servers.
- Operating System Detection: Determining the operating system running on a host, providing valuable insights into its security posture.
- Version Detection: Identifying the specific version of a service running on a host, aiding in vulnerability assessment.
- Network Mapping: Creating visual representations of network topologies, illustrating the interconnectedness of devices.
Nmap’s Essential Features for Windows Users
While Nmap’s core functionalities remain consistent across platforms, certain features are particularly valuable for Windows users:
- Native Windows Support: Nmap is available as a native Windows executable, eliminating the need for complex setups or virtual environments.
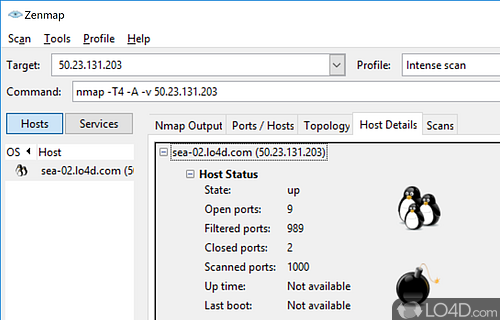
- GUI Interface (Zenmap): Zenmap provides a user-friendly graphical interface that simplifies Nmap’s complex command-line options, making it accessible to users with varying levels of technical expertise.
- Integration with Windows Tools: Nmap can seamlessly integrate with other Windows tools, such as PowerShell and the command prompt, facilitating automated scanning and analysis.
- Windows-Specific Scan Types: Nmap offers scan types specifically designed for Windows environments, such as the "Windows" scan, which utilizes Windows-specific protocols to gather information about the target.
- Script Engine: Nmap’s script engine allows users to leverage a vast library of scripts tailored to specific operating systems, services, or vulnerabilities, enhancing the depth and accuracy of network scans.
Benefits of Using Nmap on Windows
The adoption of Nmap on Windows offers a multitude of benefits for network administrators, security professionals, and anyone seeking to gain a deeper understanding of their network:
- Enhanced Network Visibility: Nmap provides a comprehensive view of the network, revealing hidden devices, open ports, and running services that might otherwise go unnoticed.
- Improved Security Posture: Nmap facilitates vulnerability assessments by identifying potential weaknesses in network devices, services, and configurations.
- Network Troubleshooting: Nmap assists in troubleshooting network connectivity issues by pinpointing the source of problems and identifying potential bottlenecks.
- Network Inventory Management: Nmap helps maintain an accurate inventory of network devices, including their operating systems, services, and configurations.
- Compliance Auditing: Nmap can be used to verify compliance with security policies and industry standards by identifying potential deviations in network configurations.
Practical Applications of Nmap on Windows
Nmap’s versatility extends to a wide range of practical applications, including:
- Network Security Audits: Identifying vulnerabilities and potential attack vectors in network devices, services, and configurations.
- Vulnerability Scanning: Detecting known vulnerabilities in operating systems, services, and applications.
- Intrusion Detection: Identifying suspicious activity on the network, such as unauthorized access attempts or malware infections.
- Network Mapping and Documentation: Creating detailed maps of network topologies and documenting network infrastructure.
- Service Discovery: Identifying and characterizing services running on network devices, facilitating network management and troubleshooting.
- Performance Monitoring: Monitoring network performance metrics, such as latency and bandwidth utilization, to identify potential bottlenecks and optimize network efficiency.
FAQs about Nmap for Windows
Q: Is Nmap legal to use?
A: Nmap is a legitimate tool for network exploration and security auditing. However, its use must comply with local laws and regulations. It is crucial to obtain proper authorization before scanning networks that you do not own or manage.
Q: How do I install Nmap on Windows?
A: Nmap can be downloaded and installed directly from the official Nmap website. The installation process is straightforward and involves running the downloaded executable file.
Q: How do I use Nmap to scan a network?
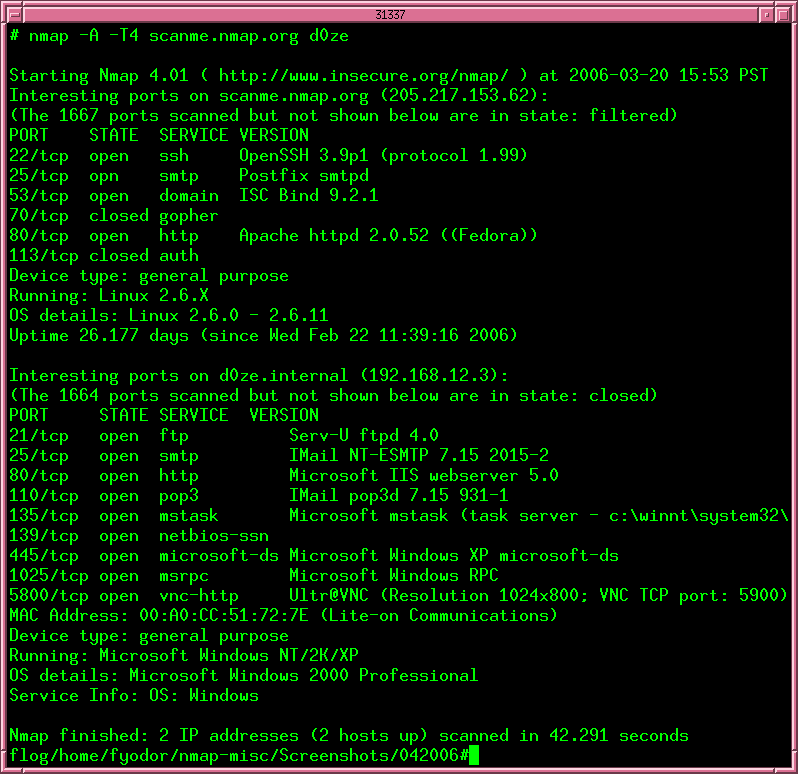
A: Nmap provides various command-line options for network scanning. For a basic scan of all hosts on a network, use the command nmap -T4 192.168.1.0/24. This command will perform a quick scan of all hosts within the specified IP address range.
Q: How do I use Nmap to identify open ports?
A: To identify open ports on a specific host, use the command nmap -sT -p 1-1024 <target IP address>. This command will perform a TCP connect scan, attempting to connect to ports 1 through 1024 on the target host.
Q: How do I use Nmap to detect the operating system of a host?
A: To detect the operating system of a host, use the command nmap -O <target IP address>. This command will perform an operating system detection scan, attempting to identify the operating system based on the host’s responses.
Q: How do I use Nmap to identify services running on open ports?
A: To identify services running on open ports, use the command nmap -sV <target IP address>. This command will perform a service version detection scan, attempting to identify the specific service running on each open port.
Tips for Using Nmap on Windows
- Start with Basic Scans: Begin with simple scans to understand Nmap’s capabilities and familiarize yourself with its syntax.
- Utilize Zenmap: Zenmap’s graphical interface simplifies Nmap’s complex command-line options, making it accessible to users with varying levels of technical expertise.
- Explore Nmap’s Script Engine: Leverage Nmap’s script engine to enhance scan capabilities and tailor them to specific needs.
- Respect Network Policies: Obtain proper authorization before scanning networks that you do not own or manage.
- Stay Informed: Keep up-to-date with the latest Nmap releases and security best practices.
Conclusion
Nmap is a powerful tool for network exploration and security auditing on Windows. Its versatility, ease of use, and comprehensive capabilities make it an indispensable resource for network administrators, security professionals, and anyone seeking to gain a deeper understanding of their network environment. By leveraging Nmap’s features and following best practices, users can enhance network visibility, improve security posture, and ensure the integrity and reliability of their network infrastructure.





Closure
Thus, we hope this article has provided valuable insights into Nmap: A Powerful Tool for Network Exploration and Security Auditing on Windows. We hope you find this article informative and beneficial. See you in our next article!
