Nmap: A Comprehensive Guide to Network Scanning with Practical Examples
Related Articles: Nmap: A Comprehensive Guide to Network Scanning with Practical Examples
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap: A Comprehensive Guide to Network Scanning with Practical Examples. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Nmap: A Comprehensive Guide to Network Scanning with Practical Examples
- 2 Introduction
- 3 Nmap: A Comprehensive Guide to Network Scanning with Practical Examples
- 3.1 Understanding the Basics of Nmap
- 3.2 Utilizing Nmap for Network Security Assessment
- 3.3 Practical Examples of Nmap Usage
- 3.4 Nmap Cheat Sheet: A Quick Reference Guide
- 3.5 FAQs Regarding Nmap Cheat Sheets
- 3.6 Tips for Effective Nmap Usage
- 3.7 Conclusion
- 4 Closure
Nmap: A Comprehensive Guide to Network Scanning with Practical Examples
Nmap, short for Network Mapper, is a powerful and versatile open-source tool that allows users to scan networks and gather information about hosts and services running on them. It is widely used by security professionals, network administrators, and researchers to assess network security, troubleshoot connectivity issues, and gather information for various purposes.
This comprehensive guide delves into the intricacies of Nmap, providing a detailed explanation of its capabilities, common usage scenarios, and practical examples to illustrate its power.
Understanding the Basics of Nmap
At its core, Nmap operates by sending specially crafted packets to target hosts and analyzing the responses. This process reveals valuable information, such as:
- Host Discovery: Determining which hosts are active on the network and their IP addresses.
- Port Scanning: Identifying open ports and the services running on them.
- Operating System (OS) Detection: Identifying the operating system running on the target host.
- Version Detection: Determining the versions of services and applications running on the target.
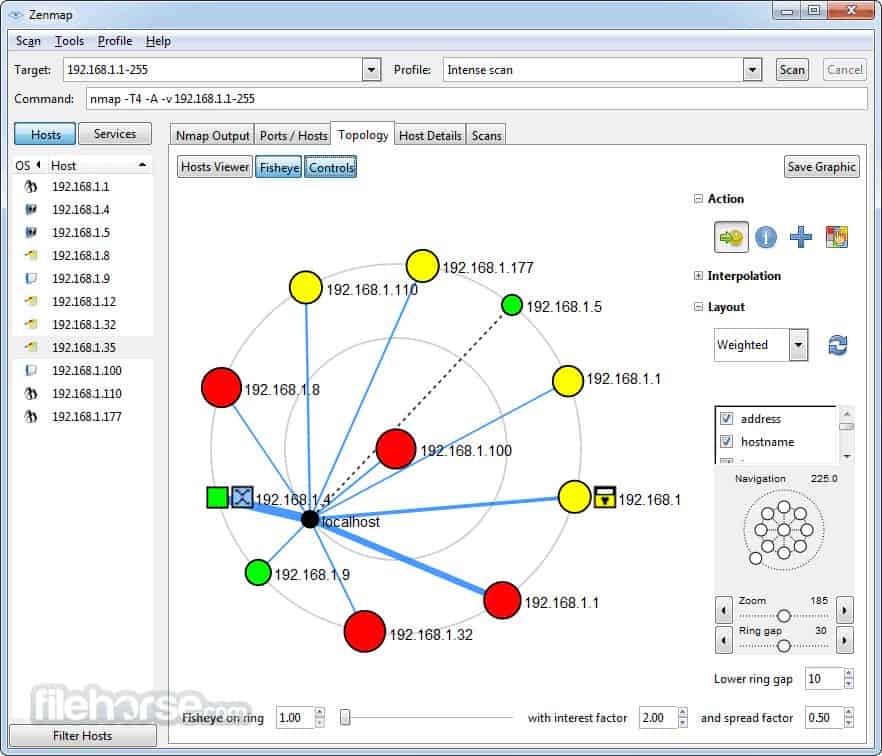
- Network Mapping: Visualizing the network topology and identifying potential vulnerabilities.
Nmap offers a wide range of scanning techniques, each tailored for specific purposes and providing different levels of detail. These techniques include:
- TCP Connect Scan: Establishes a full TCP connection to the target port.
- SYN Scan (Half-Open Scan): Sends a SYN packet, simulating a TCP connection attempt, without completing the handshake.
- UDP Scan: Sends UDP packets to target ports, checking for responses.
- FIN Scan: Sends a FIN packet, which should be rejected by a closed port, allowing for stealthy scanning.
- Xmas Scan: Sends a FIN, PSH, and URG flags, which should be rejected by a closed port, providing another stealthy scanning option.
Utilizing Nmap for Network Security Assessment
Nmap plays a crucial role in network security assessments by providing valuable insights into potential vulnerabilities. Some key applications include:
- Vulnerability Identification: Identifying open ports and services that are known to have vulnerabilities.
- Service Enumeration: Discovering the versions of services running on target hosts, which can help identify potential exploits.
- Network Mapping and Penetration Testing: Creating a detailed network map and identifying potential entry points for attackers.
Practical Examples of Nmap Usage
To illustrate the practical applications of Nmap, let’s explore some real-world scenarios:
Scenario 1: Identifying Open Ports on a Target Host
nmap -p- 192.168.1.100This command scans all ports on the host with IP address 192.168.1.100, identifying open ports and the services running on them.
Scenario 2: Detecting the Operating System of a Target Host
nmap -O 192.168.1.100This command uses Nmap’s operating system detection capabilities to identify the operating system running on the target host.
Scenario 3: Scanning a Range of IP Addresses for Open Ports
nmap -p 80,443 192.168.1.1-254This command scans all IP addresses in the range 192.168.1.1 to 192.168.1.254, specifically looking for ports 80 and 443, which are commonly used for web servers and HTTPS services.
Scenario 4: Performing a Stealthy Scan Using the FIN Scan Technique
nmap -F -sF 192.168.1.100This command performs a FIN scan on the target host, attempting to identify open ports without triggering any alerts or logging on the target system.
Nmap Cheat Sheet: A Quick Reference Guide
To simplify the process of using Nmap, various cheat sheets have been created that provide a concise overview of common commands and options. These cheat sheets typically cover the following aspects:
- Basic Scanning Techniques: Commands for host discovery, port scanning, and operating system detection.
- Advanced Scanning Techniques: Commands for stealthy scanning, vulnerability scanning, and network mapping.
- Output Formatting: Commands for customizing the output format and exporting results.
- Scripting and Automation: Commands for creating custom scripts and automating repetitive tasks.
FAQs Regarding Nmap Cheat Sheets
1. What are the benefits of using a Nmap cheat sheet?
Nmap cheat sheets offer a quick and easy way to access frequently used commands and options, saving time and effort during network scans. They are particularly useful for beginners who are still learning Nmap’s syntax and capabilities.
2. Where can I find reliable Nmap cheat sheets?
Reliable Nmap cheat sheets can be found on various online resources, including the Nmap website, security blogs, and online forums. It is important to choose resources from reputable sources to ensure accuracy and relevance.
3. How can I create my own Nmap cheat sheet?
Creating a custom cheat sheet can be a useful way to personalize the tool for specific needs. This can involve listing frequently used commands, options, and scripts, along with brief explanations and examples.
Tips for Effective Nmap Usage
- Start with basic scans: Begin by using basic commands to gather initial information about the target network.
-
Customize output formatting: Use options like
-oAand-oXto save results in different formats for analysis and reporting. - Utilize Nmap scripts: Explore the extensive library of Nmap scripts for specialized scanning tasks, such as vulnerability detection and service enumeration.
- Combine multiple techniques: Use different scanning techniques to obtain a comprehensive understanding of the target network.
- Stay updated: Regularly check for updates to Nmap and its scripts to ensure you are using the latest features and security enhancements.
Conclusion
Nmap is an indispensable tool for network security professionals, administrators, and researchers. Its versatility and comprehensive capabilities allow for effective network scanning, vulnerability assessment, and troubleshooting. By understanding the fundamental concepts and utilizing Nmap cheat sheets, users can leverage this powerful tool to gain valuable insights into their networks and enhance their security posture.
As technology continues to evolve, Nmap will likely play an even more significant role in network security. By staying informed about the latest advancements and best practices, users can maximize the potential of Nmap and ensure the security of their networks in an ever-changing digital landscape.





Closure
Thus, we hope this article has provided valuable insights into Nmap: A Comprehensive Guide to Network Scanning with Practical Examples. We appreciate your attention to our article. See you in our next article!

